Navigating a network engineer interview can be challenging, given the technical depth and breadth this role encompasses. Network engineers are the backbone of an organization's IT infrastructure and are responsible for designing, implementing, and managing effective network systems.
Consequently, interviewers seek candidates with a solid understanding of network protocols, hardware, software and problem-solving abilities to troubleshoot network issues. This guide presents a comprehensive list of common network engineer interview questions with detailed answers. The topics are derived from the skills usually required in network engineer job descriptions.
These network engineer technical interview questions cover various aspects of network engineering, providing a valuable resource for both experienced professionals seeking to refresh their knowledge and newcomers aiming to grasp what a network engineer interview might entail. Use this guide to prepare and gain confidence for your upcoming network engineer interview.
tired of job hunting?
Scroll no more. Send us your CV and we'll match it with our best remote network engineer jobs for you.
1. What is the role of a network engineer in an organization?
A network engineer, or a network architect, plays a crucial role in managing an organization's computer network. The primary responsibilities of a network engineer include designing and implementing both the hardware and software necessary for a computer network. They are tasked with understanding the organization's specific needs, planning the most effective network design to meet those needs, and managing the installation of the network systems.
Once the network is set up, network engineers are also responsible for monitoring it to ensure it performs as expected, troubleshooting any issues, and implementing necessary upgrades or repairs. They also oversee network security measures to protect sensitive data. In larger organizations, network engineers may also be involved in setting and maintaining network policies and procedures and training other staff on proper network use.
2. How would you approach a situation where a company's network is frequently experiencing downtime?
In such a situation, a systematic approach would be necessary to identify the root cause of the frequent downtime. This could involve analyzing network logs, monitoring network traffic, and checking the health of network devices. Once the cause is identified, you can decide on the appropriate measures you need to address the issue. This could involve replacing faulty hardware, updating outdated software, or even redesigning the network architecture if necessary.
3. How would you handle a situation where you need to implement a new network technology that you are unfamiliar with?
In such a situation, the first step would be to conduct thorough research to understand the new technology and how it can be integrated into the existing network. This could involve reading technical documentation, attending training sessions, or consulting with experts. The new technology should then be tested in a controlled environment before being implemented in the live network. Ongoing monitoring would also be crucial to identify and address any issues that arise.
4. Can you explain what Network Address Translation (NAT) is?
Network Address Translation (NAT) is a method used in IP networking that allows an IP address space to be remapped into another by modifying the IP address information in the IP packet headers while transiting through a traffic routing device. The most common use of NAT is for internet connection sharing. With NAT, you can use a single internet connection to provide internet access to all computers in your home or office network.
NAT works by modifying IP packets' source and/or destination addresses as they pass through a router or firewall. Most systems using NAT do so to ease accessing the internet on a private network using a single public IP address. NAT helps conserve public IP addresses by adding an additional security layer to the network due to hiding internal IP addresses from general public access.
5. Can you describe a time when you had to implement a new network security measure?
Implementing a new network security measure would typically involve a thorough understanding of the current network infrastructure and the specific security needs of the organization. The new measure should be tested in a controlled environment before being implemented in the live network. Training may also be required to ensure that all relevant staff are aware of the new measure and understand how to use it effectively.
6. How would you ensure the reliability of a network with limited resources?
Ensuring network reliability with limited resources would involve focusing on the most critical aspects of the network. This could include implementing redundancy for key network devices, regularly backing up network configurations, and monitoring network performance to identify potential issues before they cause downtime. Using cloud-based services could also be a cost-effective way to enhance network reliability.
7. How would you handle a situation where the network is slow, and users are complaining?
In such a scenario, the first step would be to identify the root cause of the slowdown. This could involve checking network utilization metrics, examining performance logs, or using network monitoring tools to identify any unusual spikes in traffic or resource usage. If a particular device or application is consuming excessive bandwidth, measures such as implementing Quality of Service (QoS) rules could be taken to manage the traffic and improve network performance.
8. Can you explain what the OSI model is?
The Open Systems Interconnection (OSI) model is a framework that describes how different network protocols interact and work together to send data over a network. The model is divided into seven layers carrying unique functions:
- Physical layer (layer 1): This is the lowest layer of the OSI model. It transmits raw bitstream over physical mediums like cables or wireless radio frequency. It deals with the electrical and mechanical specifications of the devices and media.
- Data link layer (layer 2): It is responsible for node-to-node data transfer. It provides error detection and correction to ensure data arrives at its destination without errors.
- Network layer (layer 3): This layer manages packet routing through the network. It determines the best path for data transfer between networks.
- Transport layer (layer 4): This layer provides transparent data transfer between hosts and is responsible for end-to-end error recovery and flow control.
- Session layer (layer 5) establishes, manages, and terminates connections between applications on each end. It coordinates communication sessions between devices.
- Presentation layer (layer 6): This layer transforms data into a form readable for the application layer. It formats and encrypts data to send across a network.
- Application layer (layer 7): This is the topmost layer of the OSI model. It provides network services to the user's applications. It's responsible for identifying and establishing the availability of intended communication partners and the resources required to connect with them.
9. How would you handle a situation where you need to scale up a network to handle increased traffic?
Scaling up a network to handle increased traffic would involve a thorough assessment of the current network infrastructure and the expected increase in traffic. Strategies could include adding network devices, increasing bandwidth, or implementing load balancing solutions. It would also be important to monitor the network closely after the changes are made to ensure that the network is handling the increased traffic effectively.
10. How would you manage a situation where a network upgrade disrupts business operations?
In such a situation, it would be crucial to have a rollback plan in place to revert the network to its previous state and minimize disruption. Once the network is stable, a thorough investigation would be conducted to understand why the upgrade caused disruption. The upgrade would then be adjusted based on the findings and tested thoroughly before being re-implemented.
11. Can you describe a time when you had to troubleshoot a complex network issue?
Troubleshooting a complex network issue often involves a systematic approach to isolate the problem and identify its cause. This could include examining network logs, using network monitoring and diagnostic tools, and potentially even consulting with other IT professionals or vendors. Once the issue is identified, appropriate steps can be taken to resolve it, which could range from adjusting network configurations to replacing faulty hardware.
12. How would you approach a situation where the network needs to support a new application with high bandwidth requirements?
In this scenario, a thorough assessment of the current network infrastructure would be necessary to understand its capacity to support the new application. If the current network doesn't have sufficient bandwidth, strategies such as upgrading network devices, increasing internet bandwidth, or implementing Quality of Service (QoS) rules to prioritize traffic for the new application could be considered. The network's performance should be closely monitored after the application is deployed to ensure it's operating effectively and not negatively impacting other network services.
13. How would you ensure network security for a small company with limited resources?
Ensuring network security for a small company with limited resources would involve focusing on the most critical and cost-effective measures. This could include implementing a robust firewall, ensuring all systems and software are regularly updated to patch any security vulnerabilities, and educating employees about basic security practices like strong password usage and recognizing phishing attempts. Additionally, leveraging cloud-based security solutions could provide a level of security that might otherwise be unaffordable for a small company.
14. Can you describe a situation where you had to balance network performance with network security?
Balancing network performance with network security can be a challenging task. Implementing robust security measures can sometimes impact network performance. For instance, certain types of security inspections can increase latency. However, there are ways to maintain a balance. For example, using next-generation firewalls that combine traditional firewall functions with modern network traffic filtering can provide both security and performance.
15. Can you describe a time when you had to collaborate with other IT teams to resolve a complex network issue?
Resolving a complex network issue often requires collaboration between different IT teams. For instance, a network issue could be caused by a server malfunction, requiring collaboration with the server team. Or a security issue might require working closely with the security team. Effective communication and coordination would be crucial in such situations to ensure that all teams are aligned and working towards a common goal. The network team would typically take the lead in coordinating the troubleshooting efforts, as they have the best understanding of the network infrastructure.
16. How would you handle a situation where you have to implement a major network change without causing downtime?
Implementing a major network change without causing downtime requires careful planning and testing. The change should first be tested in a non-production environment to understand its impact. The implementation should ideally be scheduled during off-peak hours to minimize potential disruption. Additionally, a rollback plan should be in place in case the change leads to unforeseen issues. Communication is also key in such situations, with all relevant parties being informed about the planned change and potential impact.
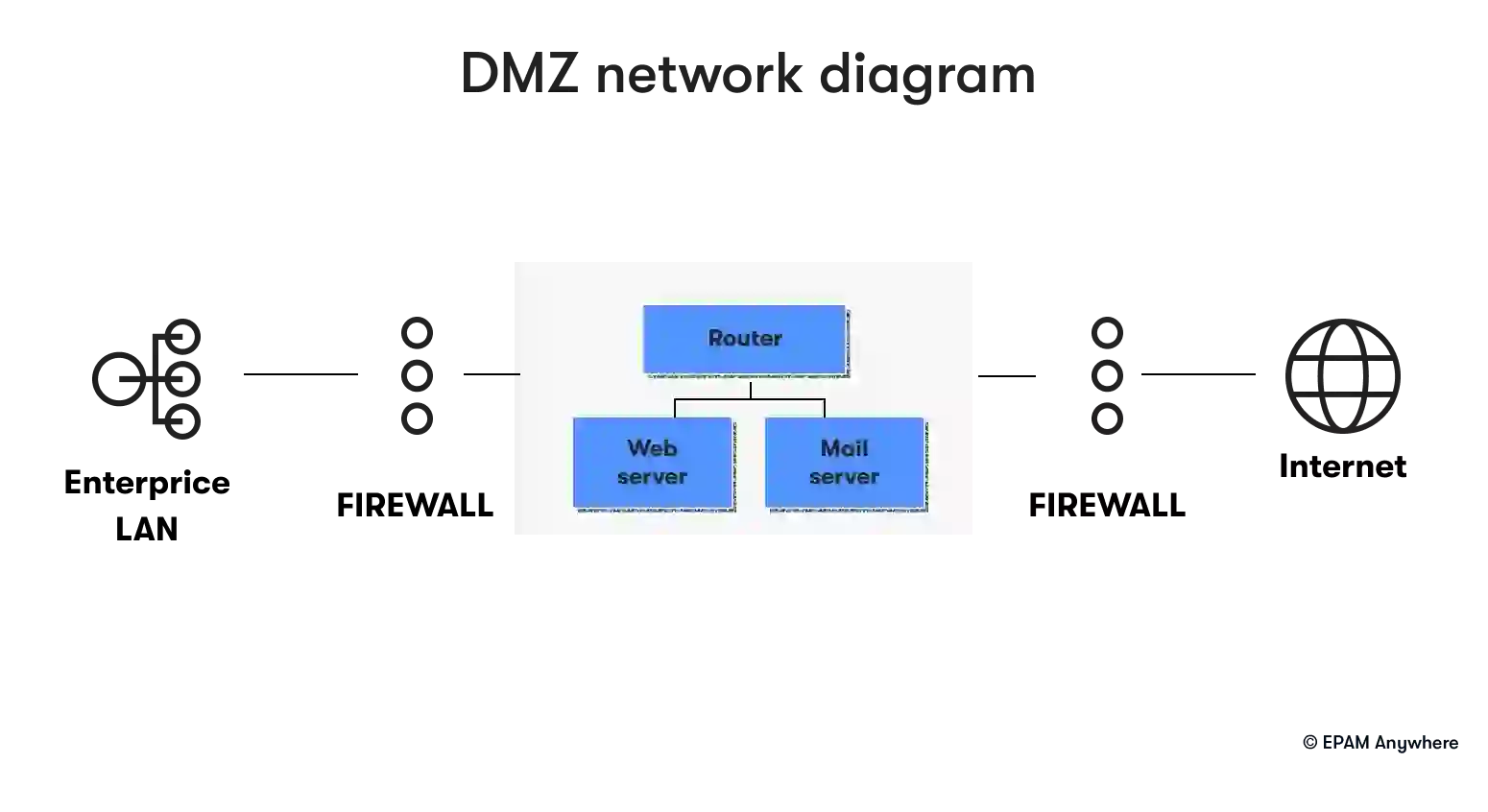
17. Can you explain what a DMZ is in networking?
In networking, a demilitarized zone (DMZ) refers to a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted network, usually the internet. The purpose of a DMZ is to add a layer of security to an organization's local area network (LAN); an external attacker only has access to equipment in the DMZ rather than the whole network.
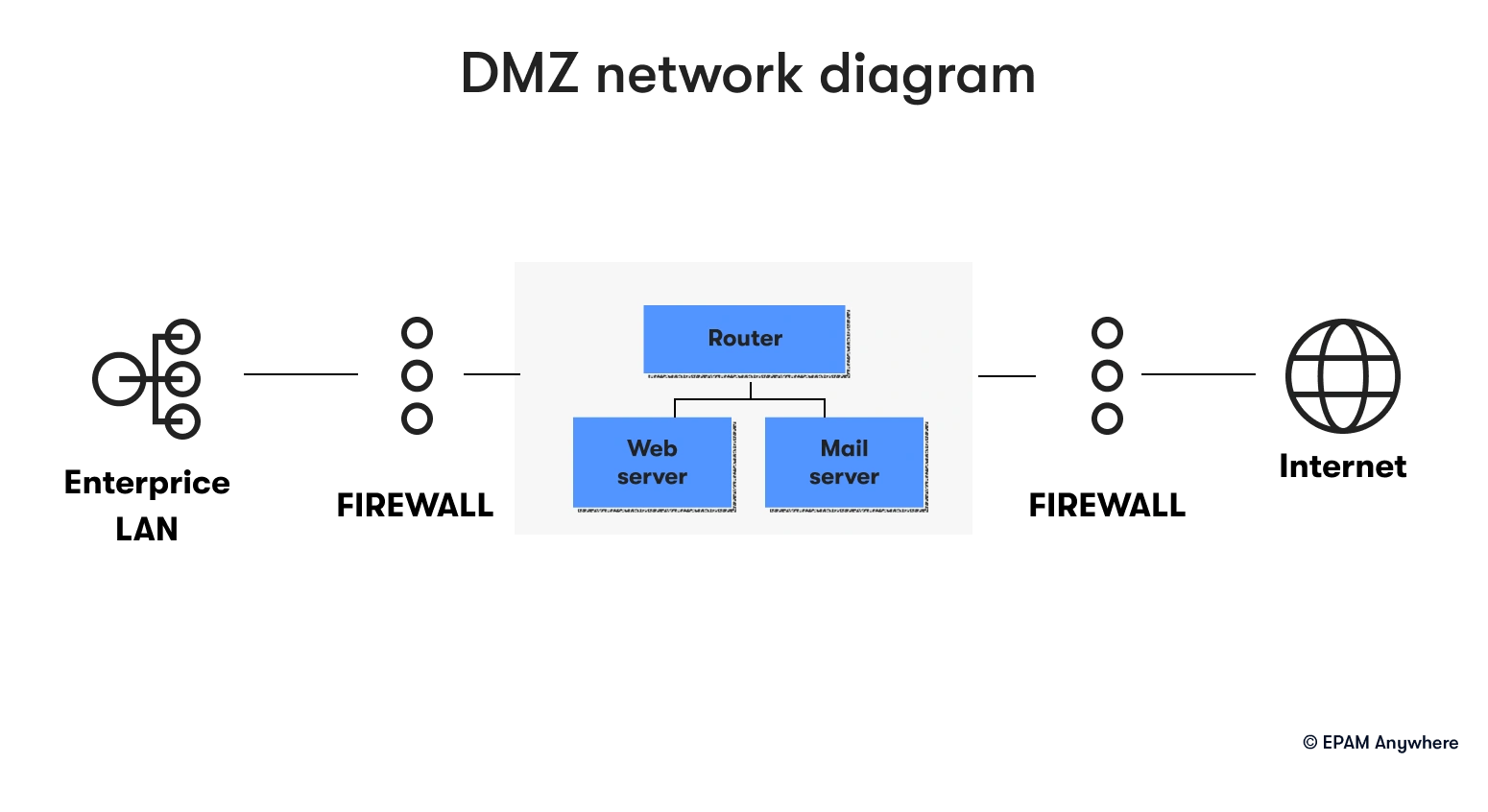
18. Can you describe a time when you had to resolve a network security breach?
Resolving a network security breach would involve a swift and coordinated response. The first step would be to contain the breach to prevent further damage. This could involve disconnecting affected systems from the network. A thorough investigation would then be conducted to understand how the breach occurred and what information may have been compromised. Measures would then be taken to address the security vulnerability that allowed the breach to occur.
19. What is the function of a DNS server in a network?
A Domain Name System (DNS) server, also known as a name server, is a server that contains a directory of domain names with their corresponding IP addresses. This system translates domain names, which are easy for people to remember, into IP addresses used by machines to identify each other on the network. This translation allows users to access websites using domain names instead of having to remember IP addresses.
20. Can you describe a situation where you had to design a network to support remote workers?
Designing a network to support remote workers would involve securing remote access, bandwidth requirements, and data security. Virtual Private Networks (VPNs) could be used to provide secure remote access, while cloud-based services could be used to provide scalable resources as needed. Data security measures such as encryption and strong authentication protocols would also be crucial.
Conclusion
In conclusion, preparing for a network engineer interview involves thoroughly understanding various networking concepts, protocols, and tools. The network engineering interview questions covered in this guide provide a comprehensive overview of what you might encounter in such an interview. Remember, the goal is to memorize these questions and answers and grasp the underlying principles and concepts.
This understanding will enable you to tackle any question confidently and demonstrate your problem-solving skills. If you're a network engineer seeking new opportunities, consider applying for remote network engineer jobs at EPAM Anywhere. We offer a wide range of projects and the chance to work with international teams, all from the comfort of your home. Start your journey with EPAM Anywhere today and advance your network engineering career.

With a focus on remote lifestyle and career development, Gayane shares practical insight and career advice that informs and empowers tech talent to thrive in the world of remote work.
With a focus on remote lifestyle and career development, Gayane shares practical insight and career advice that informs and empowers tech talent to thrive in the world of remote work.
Explore our Editorial Policy to learn more about our standards for content creation.
read more